1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
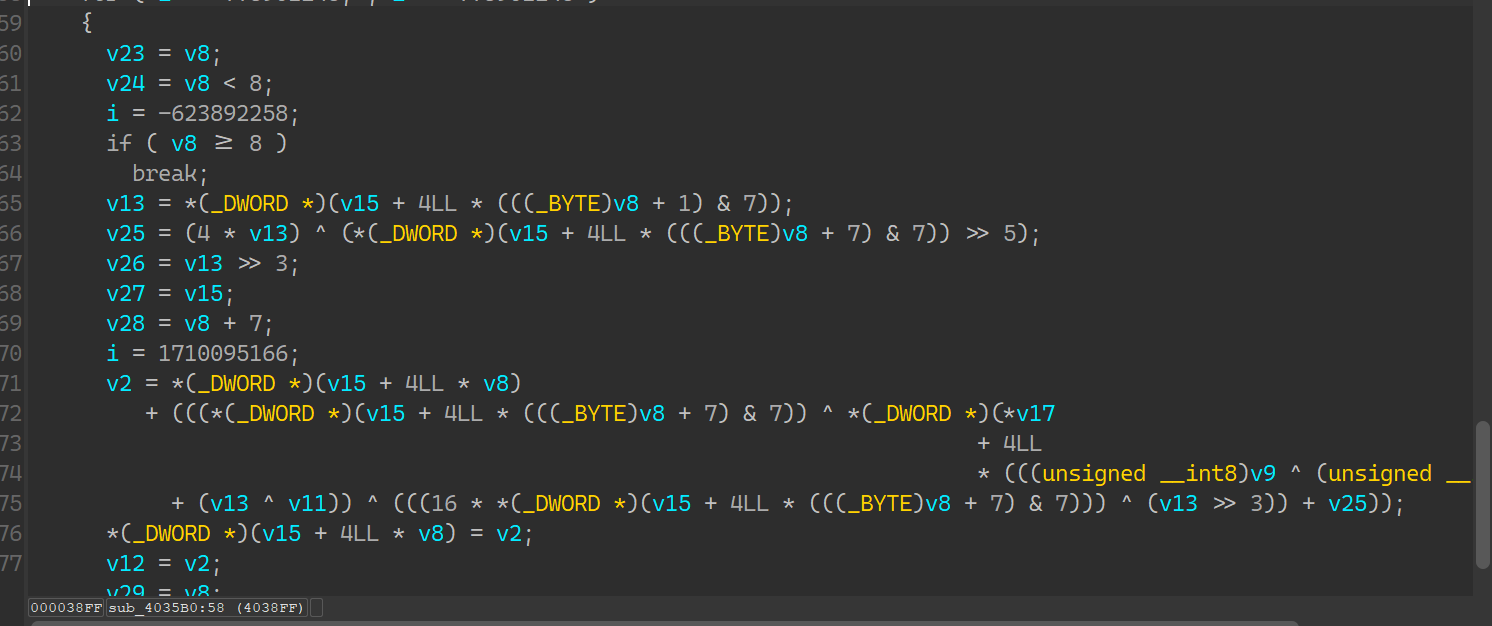
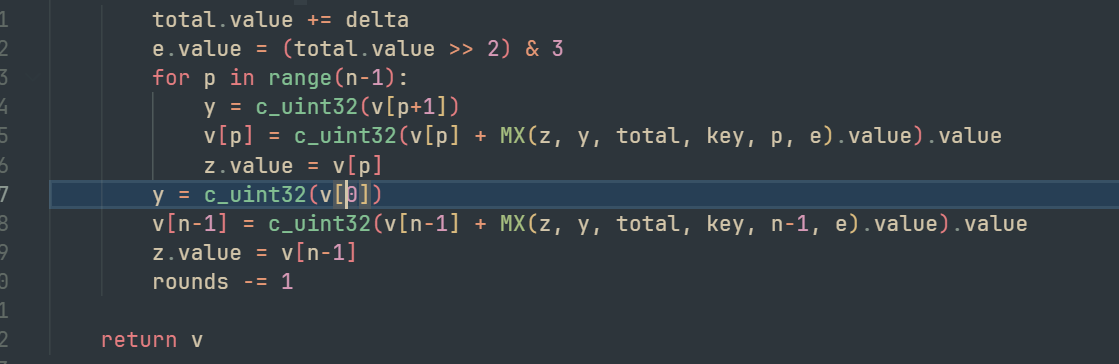
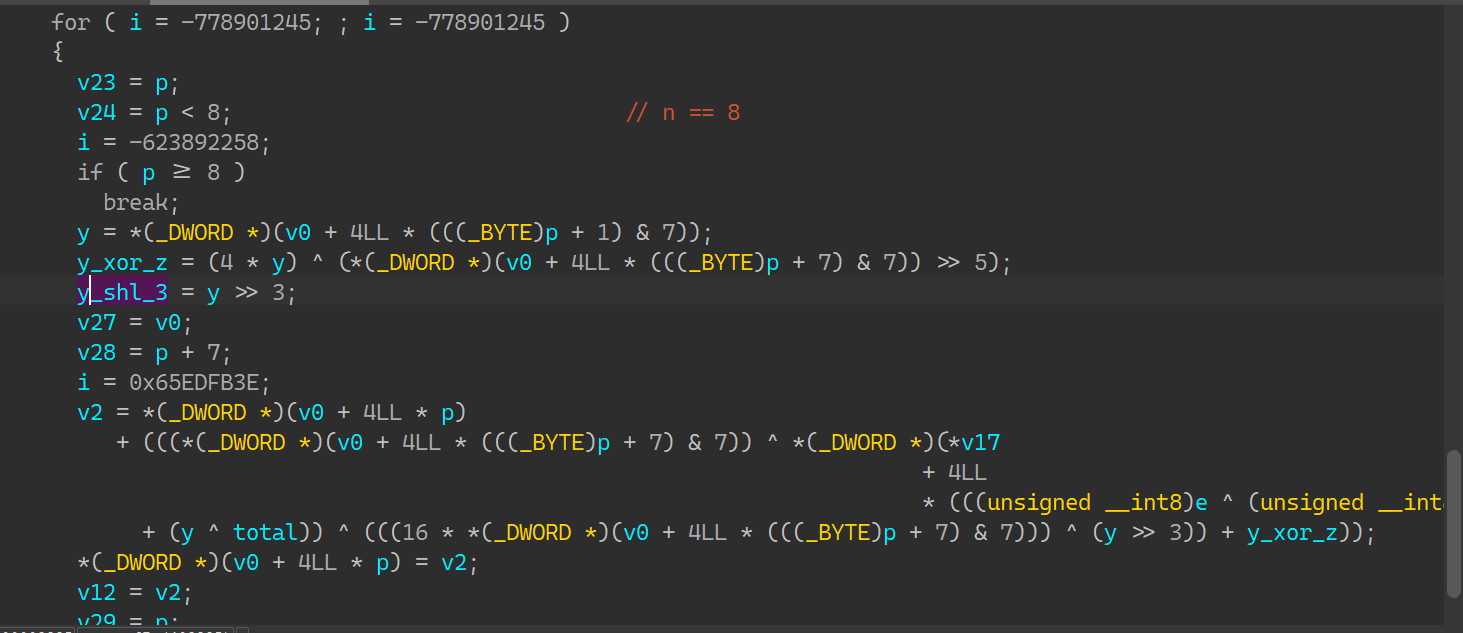
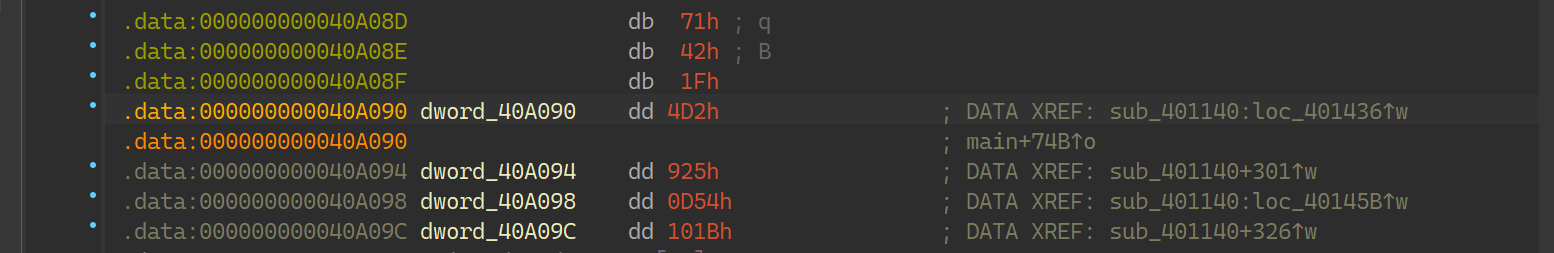
sbox = [[0x00000179, 0x000001BE, 0x243F6B50, 0x00000164, 0x243F6ABF, 0x243F6B94, 0x00000175, 0x243F6B20, 0x0000009A, 0x00000056, 0x243F6B1F, 0x000001E3, 0x243F6BE8, 0x243F6A16, 0x000000F7, 0x243F6B88, 0x000001BD, 0x000001BC, 0x243F6A41, 0x000000FB, 0x243F6B18, 0x243F6A04, 0x0000003D, 0x243F6B22, 0x000000F0, 0x00000042, 0x243F6BF5, 0x000000E0, 0x243F6A7F, 0x243F6A9A, 0x0000009C, 0x243F6A8C, 0x000001AD, 0x00000116, 0x243F6AF7, 0x000001C0, 0x243F6BBD, 0x243F6A2F, 0x0000016A, 0x0000079B, 0x243F6D8B, 0x000001CA, 0x000006A3, 0x243F6C37, 0x243F6A65, 0x243F6A6F, 0x0000018D, 0x00000617, 0x243F6DEA, 0x00000059, 0x000007CB, 0x243F6D22, 0x243F6B05, 0x243F6A2B, 0x0000007A, 0x00000717, 0x243F6CC1, 0x000001A2, 0x000007D3, 0x243F6D93, 0x243F6A5A, 0x243F6A5C, 0x00000041, 0x000007B6, 0x243F6D71, 0x00000139, 0x000006B7, 0x243F6D90, 0x243F6A2F, 0x243F6BF5, 0x00000026, 0x0000069D, 0x243F6D9A, 0x000001BF, 0x00000709, 0x243F6C54, 0x243F6AE9, 0x243F6BF7, 0x00000054, 0x00000752, 0x243F6C2C, 0x000000FA, 0x0000073A, 0x243F6C82, 0x243F6BB7, 0x243F6A09, 0x000000DA, 0x000007AF, 0x243F6C34, 0x000001E8, 0x000006E6, 0x243F6CCC, 0x243F6B05, 0x243F6AB7, 0x00000196, 0x00000693, 0x243F6C4D, 0x0000013B, 0x00000734, 0x243F6D31, 0x243F6B96, 0x243F6BD7, 0x00000110, 0x000007C2, 0x243F6DA1, 0x00000146, 0x00000795, 0x243F6C7A, 0x243F6A1F, 0x243F6A52, 0x00000087, 0x00000645, 0x243F6D74, 0x00000199, 0x00000707, 0x243F6C52, 0x243F6B1C, 0x243F6B6C, 0x00000138, 0x000006D7, 0x243F6D5C, 0x000000CA, 0x0000077A, 0x243F6DC3, 0x243F6A68, 0x243F6BC7, 0x0000008F, 0x000006CA, 0x243F6D11, 0x000001F2, 0x0000076E, 0x243F6CA9, 0x243F6A75, 0x243F6BC9, 0x00000135, 0x0000078A, 0x243F6D76, 0x00000013, 0x00000780, 0x243F6C46, 0x243F6BEB, 0x243F6A5B, 0x000000EB, 0x00000795, 0x243F6D4B, 0x0000004A, 0x000006C0, 0x243F6DDA, 0x243F6B71, 0x243F6A17, 0x000001E3, 0x00000667, 0x243F6C1B, 0x000000AF, 0x0000062A, 0x243F6DDE, 0x243F6B53, 0x243F6B4F, 0x0000019E, 0x00000613, 0x243F6D53, 0x000001EC, 0x0000076B, 0x243F6D78, 0x243F6B84, 0x243F6A1C, 0x00000009, 0x000006D8, 0x243F6CD1, 0x0000012B, 0x00000641, 0x243F6D10, 0x243F6A1C, 0x243F6A61, 0x00000104, 0x00000646, 0x243F6D6D, 0x0000000A, 0x0000061F, 0x243F6D92, 0x243F6A81, 0x243F6AE0, 0x0000017D, 0x00000666, 0x243F6C1D, 0x0000017B, 0x000007E6, 0x243F6C39, 0x243F6BE1, 0x243F6B23, 0x000000CA, 0x000006E5, 0x243F6D5A, 0x00000034, 0x0000079C, 0x243F6C18, 0x243F6B0F, 0x243F6AB2, 0x000000FC, 0x00000702, 0x243F6D7A, 0x0000005E, 0x000007D8, 0x243F6D9E, 0x243F6B03, 0x243F6A3A, 0x00000137, 0x00000619, 0x243F6C1C, 0x00000070, 0x0000071E, 0x243F6CB7, 0x243F6A42, 0x243F6A37, 0x00000150, 0x000007BB, 0x243F6D5A, 0x00000075, 0x0000071A, 0x243F6DCA, 0x243F6A48, 0x243F6B5B, 0x000001AA, 0x0000069C, 0x243F6D9D, 0x0000001B, 0x00000720, 0x243F6D57, 0x243F6B10, 0x243F6BE8, 0x000000FD, 0x00000656, 0x243F6CF4, 0x00000047, 0x00000686, 0x243F6C0B, 0x243F6BD9, 0x243F6BD8, 0x00000130, 0x000007DE, 0x243F6D74, 0x00000002, 0x000007F3, 0x243F6D4B, 0x243F6A41, 0x243F6B50, 0x00000033, 0x00000624, 0x243F6DC5, 0x00000133, 0x00000645, 0x243F6DCC, 0x243F6B43, 0x243F6B41, 0x000000E9, 0x00000753], [0x243F6D0A, 0x000000D7, 0x243F6A70, 0x243F6CA6, 0x000006A7, 0x243F6B0C, 0x000001B5, 0x00000760, 0x243F6CEB, 0x000000EE, 0x243F6ADE, 0x243F6D02, 0x00000743, 0x243F6A5C, 0x000000DC, 0x000006D9, 0x243F6DC6, 0x000001DD, 0x243F6A12, 0x243F6DFF, 0x00000732, 0x243F6B80, 0x000001AC, 0x000007D5, 0x243F6D06, 0x000000C5, 0x243F6B51, 0x243F6D2B, 0x000006DC, 0x243F6A2D, 0x00000055, 0x000006FC, 0x243F6D7D, 0x000001D0, 0x243F6AA3, 0x243F6C75, 0x0000061A, 0x243F6A2A, 0x00000101, 0x000006F0, 0x243F6C4D, 0x00000138, 0x243F6A75, 0x243F6CA9, 0x000007FC, 0x243F6B27, 0x00000123, 0x000006C5, 0x243F6D32, 0x0000003B, 0x243F6A23, 0x243F6CB3, 0x00000686, 0x243F6B1A, 0x00000107, 0x00000608, 0x243F6DFD, 0x000001E8, 0x243F6BBB, 0x243F6D08, 0x0000062B, 0x243F6B94, 0x000000A1, 0x0000075A, 0x243F6CDC, 0x000000FB, 0x243F6B69, 0x243F6DD6, 0x00000655, 0x243F6ADD, 0x000000DD, 0x000007DC, 0x243F6DBD, 0x00000068, 0x243F6B0C, 0x243F6C95, 0x00000745, 0x243F6B15, 0x000001C9, 0x00000754, 0x243F6D3A, 0x0000003D, 0x243F6B34, 0x243F6DD6, 0x000006E1, 0x243F6A4E, 0x0000004E, 0x00000776, 0x243F6D6C, 0x000000F3, 0x243F6B5D, 0x243F6CEF, 0x000007F9, 0x243F6B68, 0x000001D0, 0x000007BB, 0x243F6DC9, 0x00000164, 0x243F6A2B, 0x243F6C43, 0x00000670, 0x243F6A8A, 0x0000007B, 0x000006DC, 0x243F6DAD, 0x000000FC, 0x243F6B51, 0x243F6CE4, 0x00000760, 0x243F6AF2, 0x00000004, 0x000006B5, 0x243F6D8E, 0x0000018C, 0x243F6B3C, 0x243F6D44, 0x0000071A, 0x243F6ADD, 0x0000002E, 0x0000075A, 0x243F6DCE, 0x00000120, 0x243F6BFB, 0x243F6D9F, 0x000007B1, 0x243F6BCC, 0x00000063, 0x0000068A, 0x243F6C2D, 0x00000034, 0x243F6A0C, 0x243F6D0A, 0x000006D7, 0x243F6B8B, 0x00000112, 0x000006EE, 0x243F6DF2, 0x000000AF, 0x243F6A7C, 0x243F6C01, 0x00000628, 0x243F6B11, 0x0000005D, 0x00000657, 0x243F6CE0, 0x0000008A, 0x243F6B43, 0x243F6C86, 0x00000682, 0x243F6B31, 0x0000003B, 0x000007A5, 0x243F6CF5, 0x00000058, 0x243F6B6B, 0x243F6DA1, 0x00000657, 0x243F6B40, 0x0000008E, 0x000006F1, 0x243F6C5E, 0x00000031, 0x243F6A50, 0x243F6CBD, 0x00000721, 0x243F6BF3, 0x0000019E, 0x00000766, 0x243F6C8A, 0x0000008D, 0x243F6B1B, 0x243F6C2B, 0x0000076D, 0x243F6BCA, 0x0000019D, 0x000007BD, 0x243F6C64, 0x000001F6, 0x243F6B7C, 0x243F6D1B, 0x00000735, 0x243F6BB3, 0x000000B0, 0x000006B1, 0x243F6D6A, 0x000000DD, 0x243F6BC6, 0x243F6CC0, 0x000007E2, 0x243F6A78, 0x0000004B, 0x00000639, 0x243F6D29, 0x000001DF, 0x243F6BB1, 0x243F6CD2, 0x000006E6, 0x243F6B54, 0x000001E0, 0x000007CC, 0x243F6C8D, 0x000000C7, 0x243F6B33, 0x243F6C98, 0x00000666, 0x243F6B02, 0x000001C8, 0x0000071D, 0x243F6CC3, 0x000000BF, 0x243F6AA3, 0x243F6DE8, 0x000006E9, 0x243F6BEF, 0x000000DB, 0x00000660, 0x243F6DB8, 0x000001DD, 0x243F6BD5, 0x243F6C87, 0x0000072C, 0x243F6BAA, 0x000001F5, 0x00000663, 0x243F6DB3, 0x00000069, 0x243F6A29, 0x243F6C6A, 0x000006EB, 0x243F6B17, 0x00000137, 0x0000071B, 0x243F6CF1, 0x00000193, 0x243F6A00, 0x243F6D1A, 0x000006FF, 0x243F6B0E, 0x00000021, 0x000007B1, 0x243F6D28, 0x000001BE, 0x243F6BEA, 0x243F6DB3, 0x00000787, 0x243F6B74, 0x00000104, 0x00000736, 0x243F6CBE, 0x00000089, 0x243F6A05, 0x243F6C0C, 0x000007AE, 0x243F6A08, 0x00000142, 0x000006B0], [0x243F6DD9, 0x0000017F, 0x243F6A57, 0x0000012C, 0x243F6A21, 0x243F6B8B, 0x000000C6, 0x000018C5, 0x243F6ACE, 0x243F6C4B, 0x0000067A, 0x243F6A2B, 0x243F6F63, 0x00001C37, 0x000019D3, 0x00000114, 0x00001C6A, 0x243F73C0, 0x00001819, 0x243F740E, 0x243F7446, 0x243F73F7, 0x243F7319, 0x00000004, 0x243F683B, 0x243F7154, 0x243F6CD1, 0x00001B40, 0x000007D2, 0x00001A18, 0x243F6047, 0x000019FF, 0x243F6828, 0x0000120F, 0x243F788D, 0x00000358, 0x243F755C, 0x00001D78, 0x243F6EC0, 0x243F7510, 0x00000CB6, 0x00000259, 0x243F6AC6, 0x243F605F, 0x000010D7, 0x243F7496, 0x000006CA, 0x00001B44, 0x243F77E8, 0x243F750D, 0x00001E97, 0x243F74E5, 0x00001F57, 0x00000388, 0x000019A3, 0x243F6DF6, 0x243F74D4, 0x00000BD2, 0x243F782D, 0x00001DE7, 0x243F7596, 0x243F6E9E, 0x000005B8, 0x243F64B7, 0x243F7743, 0x243F79C4, 0x00000D70, 0x243F7230, 0x00000167, 0x00000FD2, 0x243F67CF, 0x0000028A, 0x243F6DAA, 0x00000914, 0x00000C6C, 0x000018C1, 0x243F6FD0, 0x00000D73, 0x243F7FFB, 0x000005DB, 0x243F728A, 0x0000109A, 0x243F7838, 0x243F6A4F, 0x00000590, 0x243F60EC, 0x00001ECE, 0x000018AE, 0x243F7780, 0x243F6C0D, 0x243F6944, 0x00001F7E, 0x243F6C54, 0x00001A3C, 0x243F69BD, 0x00001C8C, 0x243F6735, 0x243F6B1C, 0x00000E62, 0x243F6BAC, 0x243F77D8, 0x00000610, 0x00001C91, 0x243F72D8, 0x000002C3, 0x000006B5, 0x243F6EFD, 0x000004FA, 0x243F7964, 0x000000C1, 0x243F6B31, 0x00000FC6, 0x243F6599, 0x243F6FC0, 0x000016D1, 0x243F7E5C, 0x0000161A, 0x000001C2, 0x243F72FB, 0x00001AF6, 0x243F630A, 0x243F677E, 0x243F75A2, 0x0000008F, 0x243F612D, 0x000005C4, 0x00001739, 0x00001A95, 0x243F7163, 0x00001517, 0x243F73A9, 0x243F7B9F, 0x243F6605, 0x243F789F, 0x243F78D9, 0x243F6481, 0x00000407, 0x00001402, 0x243F76DD, 0x243F6C84, 0x243F65DE, 0x0000085E, 0x243F613E, 0x00001BE3, 0x243F6A7D, 0x000016B9, 0x00001A72, 0x243F7DE6, 0x243F6E50, 0x243F6582, 0x000001B3, 0x243F7A6A, 0x00001A0D, 0x0000195F, 0x243F6CEE, 0x243F6B4B, 0x00001517, 0x00000F71, 0x00001733, 0x00001304, 0x243F6D4A, 0x243F73EC, 0x000014C1, 0x00000D60, 0x00001A0A, 0x243F65C5, 0x243F6362, 0x000007DF, 0x0000090D, 0x000002B4, 0x243F7F3E, 0x00000E12, 0x243F7DB5, 0x243F709F, 0x243F712C, 0x243F638E, 0x243F77A0, 0x00000089, 0x243F7B1A, 0x00000763, 0x243F7C76, 0x243F6F14, 0x243F7626, 0x000009C4, 0x243F77BC, 0x243F6C86, 0x243F7FD2, 0x00000600, 0x243F76A8, 0x243F6F27, 0x0000047F, 0x000006DE, 0x243F78B8, 0x243F6DC0, 0x00001238, 0x243F7FF0, 0x243F66DE, 0x243F6E3F, 0x00000860, 0x000019ED, 0x000007B5, 0x00000C92, 0x243F70FE, 0x243F6DB7, 0x243F7049, 0x243F6BFF, 0x243F6C8F, 0x0000017F, 0x243F7510, 0x243F7C75, 0x00001AE7, 0x000015B8, 0x000009F6, 0x0000038E, 0x243F614F, 0x243F7A8B, 0x243F696F, 0x00001871, 0x243F7670, 0x243F699C, 0x243F7707, 0x243F6622, 0x243F643A, 0x000017B5, 0x0000170B, 0x00001405, 0x243F7819, 0x243F6A96, 0x243F6815, 0x00000892, 0x243F7699, 0x243F7FB6, 0x243F7F3F, 0x00000EF4, 0x243F777E, 0x000005C3, 0x0000006B, 0x00001984, 0x00001B5F, 0x000010CC, 0x00000155, 0x243F7738, 0x00001A56, 0x00000709, 0x00001DE0, 0x243F6CA6, 0x243F7F68, 0x243F7230, 0x00001280, 0x243F6E81, 0x00001078, 0x00001D32, 0x243F68BD, 0x00000818, 0x243F6311, 0x243F675C], [0x243F78C4, 0x243F753E, 0x243F736D, 0x243F75C4, 0x243F7B49, 0x243F6182, 0x243F7736, 0x487EDA66, 0x6C41AE95, 0x00000ED2, 0x243F68E7, 0x243F51D9, 0x243F4D7E, 0x00001881, 0x487EFA5B, 0x243F50D5, 0x00003A76, 0x00004BFD, 0x000042CC, 0x243F5740, 0x4881D4F4, 0x243F3454, 0x487E9D94, 0x24C0BCA1, 0x24C0A52D, 0x6C41ECE3, 0x243FAFD6, 0x00FFCA25, 0x24C0A4AC, 0x6C418D7F, 0x0000322D, 0x24C0BC9A, 0xB4418102, 0x243F458F, 0x90FE5500, 0xFC3F4317, 0xD8003DE3, 0xD880B029, 0xD88067D2, 0xFD414299, 0x6D3F9C8A, 0x680273CD, 0x4C3D6B79, 0x907ED9F3, 0xD8005409, 0x4C3D9464, 0x04BC53DA, 0x9100426C, 0x01805807, 0x4CC294D4, 0x91FD752E, 0xB4BE1640, 0x48010E11, 0xE3032424, 0xE37C4473, 0x48012FF8, 0x48014B78, 0xE37C0627, 0x8B7EECC2, 0x6C3EE5FB, 0xFC3FB6E8, 0xAB02DFA6, 0x1E3DA9CE, 0xB3FA7DB4, 0x97C4E4E9, 0x6EBFFAE7, 0x3DBE4086, 0xDB3BD655, 0x9180AE11, 0x74402D92, 0xE4C0B226, 0x417E59CF, 0x2D3E9A98, 0x74C0161F, 0x3CBED7FF, 0x65404821, 0xBA7D1866, 0x453CFEF2, 0x4EF981B4, 0x63065FB2, 0xBBF9EB62, 0x6604C332, 0xC1409279, 0xCE3B5B30, 0xA27A27C0, 0xA402D0DB, 0xA402A165, 0x6A38B205, 0x9E4030AD, 0x8143D678, 0x81BCEF4A, 0x2A01BF61, 0xC33CB9D4, 0xA58387B8, 0xA5839152, 0x5C7FE1E9, 0x79BE6BC7, 0xD6FEA602, 0x9E80BA77, 0xD4BF5F2C, 0x7403D770, 0x63C1B0E9, 0xE683FB24, 0x8806F26D, 0x313A14C9, 0xF0FDD92D, 0x257EF53D, 0x6FFBD242, 0x93BB1CE6, 0x23F9C6D3, 0x40B9FEED, 0x247C6C25, 0xA5BE678D, 0xD1056FF7, 0x41047DD2, 0x3339C309, 0x2084BA70, 0x94B8F697, 0xBFBB7643, 0xCD40FE71, 0x18C7E438, 0x9FFA5966, 0x6DFBE110, 0xD9C73A1C, 0x8E8409F9, 0x457A62B9, 0x61BB67C5, 0xA34394F8, 0x133EC8BB, 0xD4044FDD, 0x37C2F42A, 0xD27CB5F5, 0xFA4385E6, 0xDB463532, 0xE77C83DB, 0x627AF59D, 0xB2BEF94C, 0x9538FC45, 0x94C780B8, 0xCE7D1809, 0x3600DB13, 0xD4043B07, 0x823978D3, 0xC941E157, 0xCF3B9C59, 0x1BBE0DBF, 0x45B82831, 0x2FBA2022, 0xBA404B95, 0xFBC6E8E9, 0x6BB97E01, 0xFE856CA4, 0xE0F86BE2, 0x417CFCC8, 0x593E2226, 0xCFC24E4C, 0x7A0120B8, 0x497C2328, 0xDABA34D7, 0xE4FEF97A, 0x30F9F8F0, 0xA3008CE8, 0x53042AB9, 0xDCC61F48, 0x413C8D0D, 0xF58629DF, 0xFE86F2F4, 0x9D7DC3B9, 0x78C46C05, 0x0F0042A4, 0xE0C6DC69, 0xF03965FE, 0x0D392FF5, 0x96BD28CC, 0x5007B425, 0xB23A094E, 0x78C58334, 0x554534AD, 0x76BB974C, 0xCE463A66, 0x503E5C7E, 0xECC6E9D5, 0xB2BC9A65, 0x7EFA2172, 0x9CBC1C30, 0x8ABB77E4, 0xC405B76D, 0x957E308C, 0x33C63316, 0x4538C965, 0x9E7DEEC8, 0x52429D62, 0x12477299, 0x5B06AB74, 0xE230A2BD, 0xECC0E3FC, 0x3BBB450A, 0xDD08DCAF, 0x85310C1D, 0xD6BF06E5, 0x8EFA5117, 0x008ED76D, 0xE60CBBDB, 0x153F2D29, 0x40036983, 0xCECDFD2E, 0xFBB1B2D1, 0x7545E297, 0xE8358074, 0x8DF723F0, 0xA23629D2, 0x5FCBD770, 0x94BB0B3F, 0xCC884977, 0x8DF5FC17, 0xA2F3EFA9, 0x0032BD44, 0x454EB69F, 0x52361CBE, 0x284A2C50, 0x808DB6EF, 0x100C2C87, 0xC231A257, 0xF649F162, 0x34744D4A, 0xA1C8D102, 0xA4BB9290, 0xD0889351, 0x880D0584, 0xD947E8F7, 0x6773EB5C, 0x150E2584, 0x0F75E358, 0xE5F772E0, 0x9F383204, 0x75F4A824, 0x20B41979, 0x7141F2E2, 0x2889B099, 0x3A48D877, 0x0D8FEB17, 0xBB82ED5A, 0x137E775D, 0x1489F19C, 0x1D4E3534, 0xEBF75BE4, 0x638042BA, 0x88B12A5F, 0x1B731B37, 0x7340DC9D, 0x86BF7902, 0x310D3C12, 0x00F6DEFE, 0xFF3B2E2F, 0x2748AF3A, 0xC6BE79AE]
]
cipher = [0x8DF0B770, 0x4B1EB28E, 0x73C65C1C, 0x53DE48FD,
0x982EDF34, 0xD8229123, 0x90271182, 0x1F4271E7]
flag = b''
for i in range(0, len(cipher), 2):
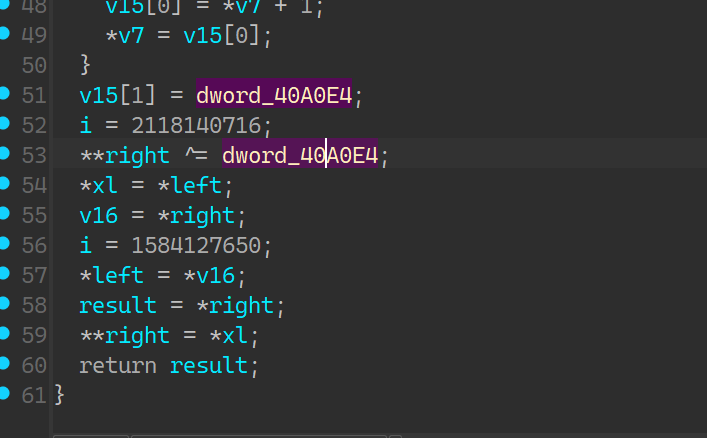
left = cipher[i+1]
right = cipher[i] ^ 0x243F6BA8
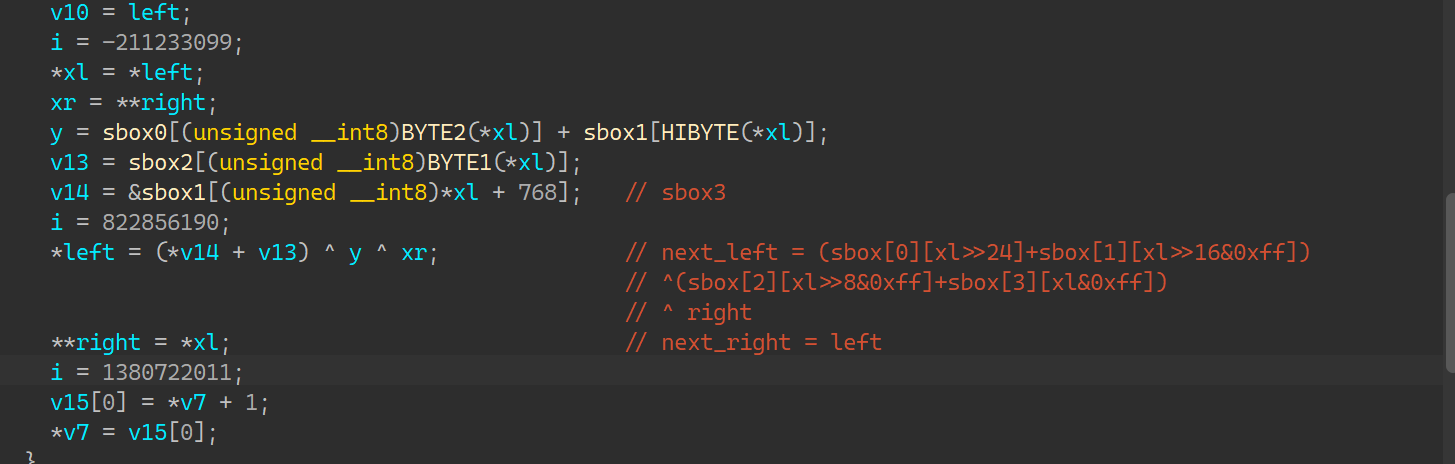
for l in range(16):
prev_left = right
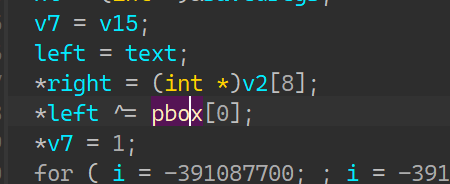
pref_right = left ^ (sbox[0][right >> 24] + sbox[1][right >> 16 & 0xff]) ^ (
sbox[2][right >> 8 & 0xff] + sbox[3][right & 0xff])
left = prev_left
right = pref_right & 0xffffffff
left ^= 0x125
flag += left.to_bytes(4, 'little') + right.to_bytes(4, 'little')
print(flag)
|